Primary Memory of Computer: Types, Features, and Functions A 2 Z detailed explanation
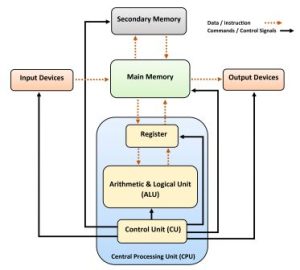
Primary Memory of Computer: Types, Features, and Functions A 2 Z detailed explanation The primary memory of computer, often referred to as “main memory” or “primary storage,” is a critical component in the functioning of a computer system. It plays a vital role in storing data and instructions that the CPU (Central Processing Unit) needs to access quickly. Understanding the primary memory of computer is essential for anyone interested in how computers work. This guide will delve into the features, types, and related terms associated with primary memory in very easy-to-understand language. What is Primary memory of computer ? The primary memory of computer is the computer’s main area where it stores data that the CPU needs to access quickly. Think of it like your short-term memory – it’s where the computer keeps the things it needs right away. This memory is much faster than secondary storage (like hard drives or SSDs), but it is also typically smaller in size. The data in primary memory is lost when the computer is turned off, making it a type of volatile memory. Types of Primary Memory The primary memory of computer is mainly divided into two types: Random Access Memory (RAM) and Read-Only Memory (ROM). 1. Random Access Memory (RAM) Random Access Memory (RAM) is the most common type of primary memory in computer. It is used to store data and programs that are currently in use so that the CPU can access them quickly. RAM is called “random access” because the CPU can read or write to any part of it without having to go through everything else first. Features of RAM: – Volatile Memory: The data in RAM is temporary and is lost when the computer is turned off. – Fast Access Speed: RAM provides fast data access, which helps in the quick execution of programs. – Temporary Storage: It is used to temporarily store the data that is currently being processed by the CPU. – Expandable: Most computers allow for RAM to be added or upgraded, which can improve performance. Types of RAM: – Dynamic RAM (DRAM): Needs to be refreshed thousands of times per second. It is slower but less expensive. – Static RAM (SRAM): Faster than DRAM but more expensive. It does not need to be refreshed as often, making it ideal for cache memory. 2. Read-Only Memory (ROM) Read-Only Memory (ROM) is another type of primary memory that, unlike RAM, is non-volatile. This means the data stored in ROM is not lost when the computer is turned off. ROM is mainly used to store the firmware, which is the software that is permanently programmed into the computer. Features of ROM: – Non-Volatile Memory: Data remains even when the computer is powered off. – Permanent Storage: Used to store firmware and critical boot-up instructions that the computer needs to start up. – Read-Only: As the name suggests, data in ROM can only be read and not written or modified easily. – Reliable: ROM is reliable for storing important data that should not change. Types of ROM: – PROM (Programmable ROM): Can be programmed once after manufacturing. – EPROM (Erasable Programmable ROM): Can be erased by exposure to ultraviolet light and reprogrammed. – EEPROM (Electrically Erasable Programmable ROM): Can be erased and reprogrammed using an electrical charge, making it more versatile. Why is Primary Memory Important? The primary memory of computer is crucial for its overall performance. Here’s why: 1. Speed: Primary memory, especially RAM, is much faster than secondary storage, allowing the CPU to quickly access and process data. 2. Efficiency: Having enough RAM enables the smooth execution of applications and operating systems. Without sufficient RAM, the computer has to use the slower secondary storage, which can significantly slow down performance. 3. Storage for Active Data: Primary memory stores the data and instructions that are currently being used by the CPU. This is essential for the efficient functioning of software applications. How Does Primary Memory Work? When you open a program on your computer, the operating system loads it into the primary memory of the computer (RAM). This allows the CPU to quickly access the data it needs to run the program. The more RAM you have, the more data and programs your computer can handle at once, making your system faster and more efficient. Understanding the primary memory of computer also involves getting familiar with some related terms: – Cache Memory: This is a small-sized type of volatile computer memory that provides high-speed data access to the processor. It acts as a buffer between the CPU and the RAM, storing frequently used data and instructions. – Memory Modules: These are printed circuit boards where memory chips are mounted. Common types include DIMM (Dual In-Line Memory Module) and SODIMM (Small Outline DIMM) for laptops. – Virtual Memory: This is a memory management capability that provides an “illusion” to users of a very large (main) memory. It is a combination of RAM and a portion of your hard drive used to simulate additional RAM. – Memory Hierarchy: This refers to a structure that uses various kinds of memory based on speed and cost to provide an efficient, cost-effective system. Benefits of Upgrading Primary Memory Upgrading the primary memory of computer can have several benefits: 1. Improved Performance: More RAM means that more data can be stored and accessed quickly, leading to faster performance in everyday tasks and when running multiple applications. 2. Better Multitasking: With more primary memory, a computer can handle more programs running simultaneously without slowing down. 3. Enhanced Gaming and Graphics: Games and graphic-intensive applications benefit greatly from increased RAM, providing smoother gameplay and quicker rendering times. Common Questions About Primary Memory 1. How Much Primary Memory Do I Need? The amount of primary memory you need depends on what you use your computer for. Basic tasks like browsing the web or using office applications can be comfortably handled with 4GB to 8GB of RAM. For more intensive tasks like gaming, video editing, or
Primary Memory of Computer: Types, Features, and Functions A 2 Z detailed explanation Read More »